TWH – Almost immediately after the draft of Justice Alito’s ruling in the Dobbs case was leaked a month before the actual decision, a number of women’s health advocates and those who provide access to abortion services began telling women to delete the apps they were using to track their menstrual cycles.
Since then there has been much debate and suggestions regarding what childbearing women could or should do if they find themselves in need of an abortion.
A number of states have indicated that prosecuting people who seek an abortion out of state remains on the table and are discussing possible legislation.
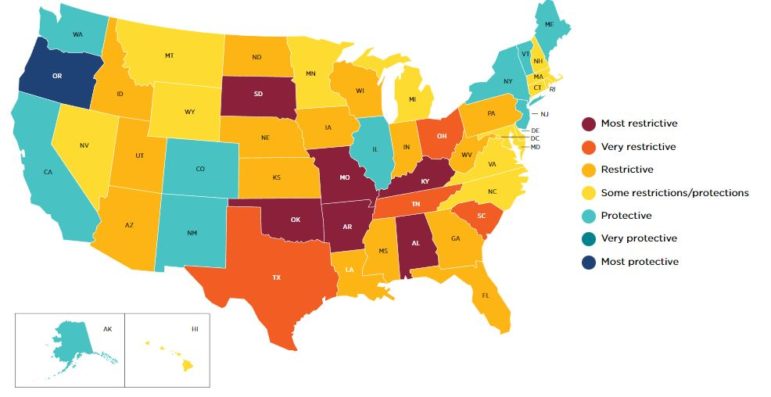
Guttmacher Institute Map of post-Roe Abortion policies – June 28, 2022
For many, navigating the path forward will depend on the state they find themselves in and which state(s) might potentially offer them the care they are seeking. But one major concern is whether some form of electronic tracking could be used to control or litigate people seeking or assisting in proving services to abortion care.
Tech Crunch reported a surge in people switching apps that are used to track menstrual cycles following the decision on Roe by the Supreme Court. The popular app, Flo which owns the lion’s share of the period tracking market at 47%, will soon offer an “anonymous mode” that will allow users to remove their personal identity from their account.
Other popular apps like Stardust, Clue, and Glow saw a large increase in the number of installations of their apps. A number of the companies issued statements about data security, and those located outside of the U.S. pointed to adhering to European privacy requirements.
However, as Mobile Health News reported, the concern over privacy within the femtech industry is not new and a recent review by the Journal of Medical Internet Research (JMIR) found that 20 out of 23 apps analyzed shared data with a third-party, and three of them collected data before gaining the consent of their users. Out of the 23 apps, only 13 or 57% provided users with information on data security.
While using pen and paper to track cycles might be the safest option, even that could have its drawbacks if a search warrant were to be issued–though there is little indication that states are moving in that direction or that most have the funding that type of action would cost when many law enforcement agencies are already understaffed.
To gain a better understanding of electronic tracking, TWH spoke with Gerald McKelvey, an eclectic Wiccan/reconstructionist Pagan who lives in Central Pennsylvania and is a mainframe programmer with 20+ years of experience in the field. McKelvey is also a Navy veteran who used to fly with VQ2, an electronic warfare squadron in North Africa, the Middle East, and the Black Sea during.
I asked McKelvey which device apps people should be the most concerned about using or having on their phones and devices.
McKelvey said, “I would be *very* cautious about what apps you install on your phone, especially given recent events. I guess the most obvious warning sign is any application that permits downloads from outside the google store (on android devices). Look under Settings > Security > Allow unknown sources. If an application is downloading something from outside the Google Playstore, then it’s probably up to no good and you should investigate further (google search can help you here).”
“Other signs of malware would be excessive battery drain, odd pop-ups you’ve never seen before, or your browser getting hijacked,” he continued, “IOS devices are somewhat more difficult to infect with malware, but always take the time to find out what services/data your applications are tracking and if you see something requesting access that makes you feel uncomfortable then I’d say trust your gut and don’t install it.”
McKelvey also pointed out the potential of using a “jailbroken” phone. Jailbreaking is a technique to remove the software restrictions put in place by the device manufacturer. While jailbreaking removes protections put in place by the manufacturer, it also means the phone is no longer linked to a given company anymore and can make the phone more difficult to identify/track.
He said, “IOS devices that have been jailbroken are probably the most vulnerable and you should be more cautious about what you install if you are using a jailbroken iPhone. I would also strongly suggest NOT using Facebook messenger on your phone, and be very careful about comments made on Facebook in general.”
A Pagan hacker who goes by Glyndower and asked not to be identified otherwise agreed and added that even base apps can reveal a person’s location. “For example, you can see your movements on Google’s location history. You must disable all location services on your phone.” They said, “It is insidious. ”
Glyndower added, “You have to go out of your way to block the reporting of location data. Another example is your photos.”
They said that during the setup of phones, something that many users now default to store services when they purchase their cellular plans, geolocation is often turned on for basic service.
“So the geotagging of photos is often a default,” they said. “It’s called EXIF data. You can find this information under the properties of a photo.” Glyndower said you can turn the feature off in the privileges given to apps.
A number of major companies have said publicly that they would cover the costs of their employees who might need to seek reproductive services outside of the state they live and work in.
However, concern over how those companies’ data might be used to potentially prosecute the employee(s) exists in this new post-Roe landscape.
In this regard, McKelvey told TWH, “Every company has the legal right to any/all information used on their devices, so anything you say on a corporate VPN or leave on a corporate laptop could be collected by a corporation.”

Image by Pete Linforth from Pixabay
A VPN is a “virtual private network” that allows users to send and receive data via a public network as though they were connected directly to a private network. The use of a VPN can help to conceal a user’s IP address and encrypts data. Many businesses use VPNs for remote workers, and most mobile devices allow for the use of a VPN.
McKelvey went on to say, “Most companies have a data use policy and make efforts to educate their employees on how personal data is collected and used. If you are not sure what your company’s IT policies are, your local HR [Human Resources] department will be able to at least point you in the right direction for clarification. Your mileage may vary!”
“There are some apps out there like Signal that allow you to communicate privately,” Glyndower added. “But now, Whatsapp – owned by Facebook/Meta – says it’s private. I have a good level of trust in Signal, but really, if you don’t want anyone to know, don’t text your shit.”
When it comes to data and how it could potentially be used against a person in a legal case, McKelvey has this to say, “Be aware of what you’re saying online, and where you’re saying it. Social media platforms like Instagram and Facebook have made it clear that they will not protect user data from a subpoena, and have implied they will assist law enforcement track women who might be breaking local laws. Assume that all communications on an open line are being monitored.”
When it comes to social media there has been ongoing concern over censorship and how big companies like Meta, the parent company of Facebook and Instagram, choose to apply their community standards and terms of service.
A recent article published by Vice suggested that using the terms “mail” in conjunction with “abortion pills” caused posts to be removed and accounts to be locked down for a period. According to the article, a Motherboard reporter had their posts removed and eventually their account banned for a brief period. Later a Facebook spokesperson said some posts had been incorrectly removed.
McKelvey said about social media and censorship, “I think social media companies will focus on profit over people, and that as consumers we should be aware that these companies see us as products.”
He also pointed out that attempts to shift the policy and actions of social media giants are likely to have challenges, “Appeals to morality or ethics will likely not move the dial with the folks who own those tech giants, so any effort to force them to change should include a financial incentive–like boycotts, online grassroots activism, class action lawsuits – again your mileage may vary.”
And when it comes to online harassment McKelvey said, “I also expect conservatives on social media to be a lot more proactive about harassing anyone they don’t like, and coordinate efforts to silence opposition. So again, be careful about what you’re saying and who’s listening. I’d suggest aggressively editing who can see your social media posts and don’t engage anyone who’s looking for an online fight. Don’t be afraid to block people, and keep those block lists up to date!”
I asked McKelvey what advice he would offer as we move forward in this new landscape.
He replied, “A lot of this is going to come down to where you live and just how much effort law enforcement wants to put into tracking people. At the extreme end of things is the Stingray network – which is a plane or helicopter with a special rig that lets them hijack cell phone communications and directly track a list of targets or filter data in real-time to locate a specific cell phone in any given area. But that’s expensive to operate and not every state uses the technology.”
McKelvey continued, “At the lower end of things are bots that scrape social media and look for key phrases and medical terminology and generate a report based on what they find. There are many ways to track information and find people via technology but these days there’s almost too much data out there.”
He explained and concluded with, “The issue isn’t finding data, it’s sorting it into something useful. So if you’re going to talk about abortion, health care, or birth control, some tips on hiding ‘under the radar’ would be to use abbreviations instead of full terminology. You could also deliberately misspell words (some bots can’t spell worth a darn!) and use slang/codewords to get around the search filters.”
Glyndower said, “I’m very suspicious so my best advice is to limit your communication. Tell only people you trust where you are going, don’t leave an out-of-office reply, and if you want to travel privately, get a low-tech burner phone for an emergency and keep it off. Leave your regular phone at home and leave it on with location services active. Where you are going is your business and no one else.”
How states will ultimately choose to react and respond to the demise of Roe remains to be seen. How proposed legislation is drafted and signed into law and those laws are applied and interpreted has also yet to be determined. The best we can all do is to stay informed and adjust accordingly.
The Wild Hunt is not responsible for links to external content.
To join a conversation on this post:
Visit our The Wild Hunt subreddit! Point your favorite browser to https://www.reddit.com/r/The_Wild_Hunt_News/, then click “JOIN”. Make sure to click the bell, too, to be notified of new articles posted to our subreddit.